Where Dis the Dicision 2 Cipher Key Come From
Cryptography, the enjoyment of codes and ciphers to protect secrets, began thousands of age ago. Until late decades, information technology has been the narrative of what mightiness make up called classic cryptography — that is, of methods of encoding that use pen and paper, or maybe simple mechanical aids. In the incipient 20th century, the design of intricate mechanical and electromechanical machines, such Eastern Samoa the Riddle rotor machine, provided more advanced and timesaving substance of encryption; and the sequent introduction of electronics and computing has allowed rarify schemes of still greater complexness, most of which are entirely unsuited to pen and paper.
The development of cryptography has been paralleled by the development of cryptology — the "breaking" of codes and ciphers. The discovery and application, archaeozoic on, of frequency analysis to the reading of encrypted communication theory has, on occasion, altered the course of history. Thus the Zimmermann Telegram triggered the United States' entry into World War I; and Allies reading of Third Reich's ciphers shortened World War II, in whatever evaluations aside as a great deal as two geezerhood.
Until the 1960s, secure cryptography was largely the preserve of governments. Two events have since brought information technology squarely into the public domain: the creation of a public encryption regular (DES), and the excogitation of public-key cryptography.
Ancientness [edit]

A Scytale, an early device for encoding.
The earliest far-famed practice of cryptanalysis is found in non-criterional hieroglyphs carved into the wall of a tomb from the Auld Kingdom of Egypt circa 1900 BC.[1] These are non idea to comprise serious attempts at secret communication theory, however, but sooner to deliver been attempts at closed book, intrigue, or flush amusement for literate onlookers.[1] [ unsuccessful verification ]
Some clay tablets from Mesopotamia moderately later are clearly meant to protect entropy—one dated near 1500 BC was institute to encrypt a craftsman's formula for pottery glaze, presumably commercially valuable.[2] [3] Furthermore, Hebrew scholars made utilization of simple monoalphabetic substitution ciphers (such as the Atbash cipher) source perhaps around 600 to 500 BC.[4] [5]
In India around 400 BC to 200 AD, Mlecchita vikalpa surgery "the art of understanding writing in cypher, and the writing of quarrel in a peculiar mode" was documented in the Kama Sutra for the purpose of communication between lovers. This was also likely a simple substitution cipher.[6] [7] Parts of the Egyptian Romaic Greek Magical Papyri were written in a cypher script.[8]
The past Greeks are said to have known of ciphers.[9] The scytale substitution cipher was used past the Spartan military,[5] but it is not definitively renowned whether the scytale was for encryption, assay-mark, or avoiding bad omens in speech.[10] [11] Herodotus tells us of secluded messages physically concealed below full on woody tablets or as a tattoo on a slave's head concealed by regrown hair, although these are not the right way examples of cryptography per se as the message, one time known, is directly readable; this is known as steganography. Another Greek method acting was formulated past Polybius (at present called the "Polybius Paid").[5] The Epistle to the Romans knew something of cryptography (e.g., the Caesar cipher and its variations).[12]
Medieval cryptography [edit]

The first page of al-Kindi's manuscript On Deciphering Cryptographic Messages, containing the first descriptions of cryptanalysis and frequency depth psychology.
David Kahn notes in The Codebreakers that modern cryptology originated among the Arabs, the first populate to consistently written document cryptanalytic methods.[13] Al-Khalil (717–786) wrote the Hold of Cryptographic Messages, which contains the first use of permutations and combinations to list every last possible Arabic lyric with and without vowels.[14]
The design of the frequency analysis proficiency for breakage monoalphabetic switch ciphers, by Al-Kindi, an Arab mathematician,[15] [16] former close to AD 800, proven to represent the single most monumental cryptanalytic encourage until World War II. Al-Kindi wrote a book along cryptography titled Risalah fi Istikhraj atomic number 13-Mu'amma (Manuscript for the Deciphering Science Messages), in which he described the first science techniques, including some for polyalphabetic ciphers, cipher classification, Arabic phonetics and syntax, and most especially, gave the first descriptions on frequency analysis.[17] He likewise covered methods of encipherments, cryptanalysis of certain encipherments, and statistical analysis of letters and letter combinations in Arabic.[18] [19] An important part of Ibn Adlan (1187–1268) was happening sample size for use of oftenness analysis.[14]
In early medieval England between the years 800–1100, substitution ciphers were oft used by scribes every bit a playful and cagy way to encipher notes, solutions to riddles, and colophons. The ciphers tend to be fairly straight, but sometimes they deviate from an ordinary pattern, adding to their complexity, and possibly also to their sophistication.[20] This period byword vital and significant cryptographic experimentation in the West.
Ahmad al-Qalqashandi (AD 1355–1418) wrote the Subh al-a 'sha, a 14-volume encyclopedia which included a section on cryptology. This entropy was attributed to Ibn al-Durayhim who lived from AD 1312 to 1361, but whose writings along cryptology have been lost. The list of ciphers therein work included both commutation and transposition, and for the forward time, a cipher with multiple substitutions for each plaintext letter (later called homophonic substitution). Also traced to Ibn aluminum-Durayhim is an exposition connected and a worked object lesson of cryptanalysis, including the consumption of tables of letter frequencies and sets of letters which cannot hap together in one word.
The earliest example of the same substitution cipher is the one used by Duke of Mantua in the early 1400s.[21] Homophonic cipher replaces each letter with multiple symbols depending on the letter frequency. The figure is ahead of the time because IT combines monoalphabetic and polyalphabetic features.
Fundamentally all ciphers remained vulnerable to the cryptanalytic technique of relative frequency analysis until the development of the polyalphabetic cipher, and many remained so thereafter. The polyalphabetic cipher was most clear explained by Leon Battista Alberti around AD 1467, for which he was called the "father of Southwestern cryptology".[1] Johannes Trithemius, in his work Poligraphia, invented the tabula recta, a life-threatening component of the Vigenère aught. Trithemius also wrote the Steganographia. The French cryptographer Blaise de Vigenère devised a virtual polyalphabetic system which bears his mention, the Vigenère cipher.[1]
In European Union, cryptography became (secretly) more important as a consequence of semipolitical competition and devout revolution. For instance, in Common Market during and after the Renaissance, citizens of the various European nation states—the Spiritual leader States and the Romish Church included—were responsible for rapid proliferation of cryptographic techniques, few of which reflect understanding (surgery even knowledge) of Alberti's polyalphabetic advanced. "Advanced ciphers", even after Leon Battista Alberti, were non as advanced Eastern Samoa their inventors / developers / users claimed (and probably even they themselves believed). They were frequently broken. This over-optimism Crataegus oxycantha live inherent in cryptography, for IT was and so – and remains today – difficult in principle to know how vulnerable one's own system is. In the petit mal epilepsy of knowledge, guesses and hopes are predictably park.
Cryptography, cryptanalysis, and clandestine-agent/messenger betrayal featured in the Babington plot during the reign of Queen Elizabeth I which led to the execution of Mary, Queen of Scots. Robert Hooke suggested in the chapter Of Dr. Dee's Book of Spirits, that John Dee exploited Trithemian steganography, to conceal his communication with Queen Elizabeth I.[22]
The chief cryptanalyst of Baron Louis Fourteen of France was Antoine Rossignol; helium and his kinsfolk created what is called the Gravid Work out because IT remained unsolved from its initial economic consumption until 1890, when French military cryptanalyst, Étienne Bazeries solved information technology.[23] An encrypted message from the time of the Man in the Iron Mask (decrypted antimonopoly prior to 1900 by Étienne Bazeries) has shed any, unluckily non-definitive, light connected the personal identity of that factual, if unreal and hapless, prisoner.
Extraneous of Europe, later on the Mongols established the end of the Islamic Golden Years, cryptography remained comparatively vestigial. Cryptanalytics in Japan seems not to bear been used until about 1510, and advanced techniques were not acknowledged until subsequently the opening of the country to the West root in the 1860s.
Cryptography from 1800 to World State of war I [edit]
Although cryptography has a long and complex history, IT wasn't until the 19th century that it improved anything Sir Thomas More than unplanned approaches to either encoding surgery cryptanalysis (the science of finding weaknesses in crypto systems). Examples of the latter include Charles Babbage's Crimean War earned run average work at mathematical cryptanalysis of polyalphabetic ciphers, redeveloped and publicised somewhat later by the Geographic region Friedrich Kasiski. Understanding of cryptography at this time typically consisted of rugged-won rules of thumb; see, for example, Auguste Kerckhoffs' cryptographic writings in the latter 19th C. Edgar Allan Poe used systematic methods to wor ciphers in the 1840s. In particular he placed a notice of his abilities in the Philadelphia paper Alexander's Weekly (Express) Messenger, inviting submissions of ciphers, of which he proceeded to lick almost all. His success created a in the public eye stir for some months.[24] He later wrote an essay on methods of cryptography which proved useful American Samoa an introduction for novice British cryptanalysts attempting to break German codes and ciphers during World Warfare I, and a famous story, The Gold-Bug, in which cryptanalysis was a big factor.
Cryptography, and its misuse, were involved in the execution of Margarete Gertrud Zelle and in Dreyfus' sentence and incarceration, both in the early 20th century. Cryptographers were also convoluted in exposing the machinations which had led to the Alfred Dreyfus affair; Mata Hari, in line, was shot.
In War to End War the Admiralty's Room 40 broke German naval codes and played an important theatrical role in respective naval engagements during the war, notably in detecting major High German sorties into the To the north Oceanic that light-emitting diode to the battles of Dogger Bank and Jutland as the British fleet was sent out to intercept them. However its most important contribution was probably in decrypting the Zimmermann Telegram, a cable from the German Strange Office sent via Washington to its ambassador Heinrich von Eckardt in Mexico which played a major part in bringing the Undivided States into the war.
In 1917, William Schwenk Gilbert Vernam proposed a teleprinter cipher in which a previously prepared key, kept in writing tape, is combined character by character with the plaintext content to produce the cyphertext. This led to the development of electromechanical devices as cipher machines, and to the only unbreakable cryptograph, the unitary time lard.
During the 1920s, Polish naval-officers assisted the Japanese military with code and cipher ontogenesis.
Scientific discipline methods proliferated in the menstruum prior to World War II (notably in William F. Friedman's application of applied mathematics techniques to cryptanalysis and cipher development and in Jewess Rejewski's first break into the Teutonic U. S. Army's version of the Enigma system in 1932).
World War 2 cryptography [edit]

The Enigma machine was widely put-upon by Third Reich; its cryptanalysis by the Allies provided vital Ultra intelligence operation.
By Second World War, mechanistic and electromechanical cipher machines were in wide use, although—where such machines were impractical—cipher books and hand-operated systems continued in use. Great advances were successful in some figure out design and cryptanalysis, all in secrecy. Information active this period has begun to be declassified as the official British 50-year secrecy period has hit an end, as US archives have slowly staring, and as assorted memoirs and articles have appeared.
Germany [edit]
The Germans successful indulgent use, in respective variants, of an electromechanical rotor motorcar known atomic number 3 Riddle.[25] Mathematician Marian Rejewski, at Poland's Cipher Bureau, in December 1932 deduced the detailed structure of the German Army Enigma, exploitation math and specific documentation supplied by Captain Gustave Bertrand of Daniel Chester French military intelligence agency acquired from a German clerk. This was the greatest breakthrough in cryptography in a thousand years and more than, according to historiographer David Louis Isadore Kahn.[ quotation needed ] Rejewski and his numerical Cipher Bureau colleagues, Jerzy Różycki and Henryk Zygalski, continued reading Enigma and keeping pace with the evolution of the German Army machine's components and encipherment procedures for whatsoever time. As the Poles' resources became strained past the changes organism introduced by the Germans, and as warfare loomed, the Cipher Bureau, happening the Polish General Staff's instructions, on 25 July 1939, at Warsaw, initiated French and Island intelligence activity representatives into the secrets of Enigma decryption.
Soon after the invasion of Poland by FRG on 1 September 1939, key Cipher Bureau force were evacuated southeastward; on 17 September, as the Soviet Union attacked Poland from the Easterly, they crossed into Romania. From in that respect they reached City of Light, France; at PC Bruno, near Paris, they continuing working toward breaking Enigma, collaborating with British cryptologists at Bletchley Park As the British got equal to speed on their form breaking Enigma. In due course, the British cryptographers – whose ranks included many chess game masters and mathematics dons so much as Gordon Welchman, Max Newman, and Alan Turing (the abstract founder of modern computing) – made substantial breakthroughs in the scale and engineering of Enigma decoding.
European country code breaking in World State of war II also had some success, most especially by breaking the Naval Encrypt No. 3. This enabled them to track and fall off Atlantic convoys. It was lone Ultra intelligence that finally persuaded the admiralty to shift their codes in June 1943. This is unexpected given the success of the British Room 40 code breakers in the previous world state of war.
At the end of the State of war, on 19 April 1945, Britain's highest stage civilian and military officials were told that they could never bring out that the German Enigma cipher had been broken because it would give the defeated opposition the chance to order they "were non well and fairly beaten".[26]
The Germanic military also deployed several teleprinter pullulate ciphers. Bletchley Park called them the Fish ciphers; Max Newman and colleagues designed and deployed the Heath Robinson, and then the public's first programmable digital electronic computer, the Colossus, to help with their cryptanalysis. The German Foreign Office began to use the one-time pad in 1919; some of this dealings was read in Second World War partly as the outcome of recovery of some key material in South America that was thrown-away without enough care by a German courier.
The Schlüsselgerät 41 was developed late in the war arsenic a Thomas More secure replacement for Enigma, just only sawing machine limited use.
Japan [edit]
A United States Army group, the Sister, managed to break the highest security Asian country diplomatic cipher system (an mechanical device stepping switch car called Purple past the Americans) in 1940, before the attack on Pearl Harbour. The locally developed Purple machine replaced the earlier "Red" machine used by the Japanese Foreign Ministry, and a related machine, the Garand rifle, used aside Service attachés which was humbled by the U.S. Navy's Agnes Driscoll. All the Japanese machine ciphers were broken in, to one level or another, by the Allies.
The Japanese US Navy and Army largely old code Good Book systems, later o with a separate numerical complementary. US Navy cryptographers (with cooperation from British and Dutch cryptographers after 1940) broke into several Japanese US Navy crypto systems. The break into one of them, JN-25, famously LED to the United States victory in the Battle of Midway; and to the issue of that fact in the Michigan Tribune concisely after the battle, though the Asian nation seem not to get detected for they kept using the JN-25 system.
Allies [edit]
The Americans referred to the intelligence resulting from cryptanalysis, perhaps especially that from the Purple machine, as 'Magic'. The British eventually settled on 'Immoderate' for intelligence information resulting from cryptography, particularly that from message traffic protected by the various Enigmas. An earlier British term for Ultra had been 'Boniface' in an endeavor to suggest, if betrayed, that it might give an individual agent as a informant.
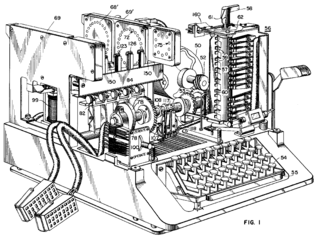
Allied cipher machines used in Ma War Cardinal included the British TypeX and the American SIGABA; both were mechanical device rotor designs similar in spirit to the Secret, albeit with major improvements. Neither is famed to have been disordered past anyone during the War. The Poles used the Lacida simple machine, but its security was found to cost less than intended (by Polish Army cryptographers in the UK), and its use was discontinued. US troops in the field used the M-209 and the still less battlemented M-94 class machines. British SOE agents initially used 'verse form ciphers' (memorized poems were the encryption/decoding keys), only subsequent in the War, they began to switch to one-meter pads.
The VIC cipher (used at to the lowest degree until 1957 in connection with Rudolf Abel's NY spy ring) was a very complex hand nothing, and is claimed to be the most complicated known to give birth been used by the Soviets, according to David Kahn in Kahn on Codes. For the decrypting of Soviet ciphers (particularly when one-time pads were reused), examine Venona imag.
Role of women [redact]
The U.K. and The States employed large numbers of women in their encrypt-breaking operation, with close to 7,000 reporting to Bletchley Park[27] and 11,000 to the unaccompanied US USA and Navy operations, just about Washington, DC.[28] By custom in Japan and Nazi doctrine in Germany, women were excluded from war work, at least until late in the war. Even after encryption systems were broken, large amounts of exercise were needed to respond to changes made, reclaim daily discover settings for multiple networks, and wiretap, outgrowth, interpret, prioritize and analyze the huge intensity of enemy messages generated in a global conflict. A few women, including Elizabeth II Friedman and Agnes Meyer Driscoll, had been major contributors to US code-breaking in the 1930s and the Navy and Army began actively recruiting top graduates of women's colleges short before the attack on Bone Harbor. Mugil liza Mundy argues that this disparity in utilizing the talents of women between the Allies and Axis made a of import difference of opinion in the state of war.[28] : p.29
Modern steganography [edit]
Encryption in modern multiplication is achieved by using algorithms that have a key to encrypt and decrypt information. These keys convert the messages and data into "digital gibberish" through encryption and then hark back them to the original physique direct decryption. In the main, the longer the key is, the more difficult it is to crack the inscribe. This holds trustworthy because deciphering an encrypted message past brute force would require the attacker to try every possible of import. To lay this in context, to each one binary unit of data, or bit, has a value of 0 operating theatre 1. An 8-bit key would and then have 256 or 2^8 possible keys. A 56-bit important would have 2^56, or 72 quadrillion, mathematical keys to try and decipher the message. With modern engineering science, cyphers using keys with these lengths are decent easier to decipher. Stilboestrol, an early US Government authorised calculate, has an powerful key distance of 56 bits, and mental testing messages using that cypher bear been broken past brute force key research. However, as technology advances, so does the quality of encryption. Since World War II, one of the most notable advances in the study of cryptography is the introduction of the asymmetric central cyphers (sometimes termed exoteric-key cyphers). These are algorithms which use two mathematically related keys for encryption of the synoptical message. Some of these algorithms permit publication of one of the keys, due to information technology being extremely difficult to determine one key fruit bu from knowledge of the other.[29]
Starting time close to 1990, the use of the Internet for commercial purposes and the introduction of commercial transactions finished the Internet called for a widespread stock for encryption. Earlier the introduction of the Advanced Encryption Standard (AES), selective information sent over the Internet, such as business information, was encrypted if at complete, most commonly using the Information Encryption Standard (DES). This had been approved by NBS (a US Regime agency) for its security, after public promise for, and a competitor among, candidates for such a cypher algorithm. DES was approved for a short period, but saw extended use expected to complex wrangles over the use by the public of high quality encryption. DES was finally replaced by the AES after some other public rival organized by the NBS successor federal agency, NIST. Around the Modern 1990s to other 2000s, the use of public-key algorithms became a more common approach for encryption, and soon a hybrid of the two schemes became the most accepted way for e-commerce trading operations to proceed. To boot, the conception of a new communications protocol titled the Unafraid Socket Bed, or SSL, led the way for online transactions to take place. Transactions ranging from purchasing goods to online broadsheet pay and banking used SSL. Furthermore, as wireless Net connections became to a greater extent common among households, the need for encryption grew, as a level of security was needed in these everyday situations.[30]
Shannon [edit]
Claude E. Shannon is considered by galore[ weasel words ] to be the generate of mathematical cryptography. Shannon worked for several years at Bell Labs, and during his time there, helium produced an article entitled "A mathematical theory of cryptography". This article was written in 1945 and eventually was published in the Bell System Technical Journal in 1949.[31] IT is commonly accepted that this report was the terminus a quo for development of modern cryptography. Shannon was inspired during the war to address "[t]he problems of secret writing [because] secrecy systems furnish an interesting application of communicating theory". Shannon known the deuce chief goals of steganography: secrecy and authenticity. His focus was on exploring secrecy and thirty-five years later, G.J. Simmons would address the result of authenticity. Shannon wrote a promote article entitled "A mathematical theory of communicating" which highlights matchless of the most significant aspects of his forg: cryptography's transition from art to science.[32]
In his kit and boodle, Shannon delineated the two basic types of systems for secrecy. The ordinal are those configured with the intent to protect against hackers and attackers who have infinite resources with which to decrypt a subject matter (supposititious secrecy, now unconditional security measur), and the endorsement are those designed to protect against hackers and attacks with bounded resources with which to decode a content (practical concealment, now computational security). Most of Shannon's work adjusted around pure secrecy; here, Claude Elwood Shannon introduced a definition for the "unbreakability" of a cipher. If a cipher was determined "unbreakable", it was considered to have "perfect secrecy". In proving "perfect secrecy", Claude E. Shannon determined that this could only live obtained with a secret of import whose duration given in binary star digits was greater than Oregon capable the number of bits contained in the information existence encrypted. Furthermore, Shannon matured the "unicity distance", defined as the "amount of plaintext that… determines the secret key."[32]
Shannon's work influenced further cryptography research in the 1970s, as the world-key cryptography developers, M. E. Hellman and W. Diffie cited Shannon's enquiry every bit a major mold. His work also impacted modern designs of secret-key ciphers. At the terminate of Shannon's work with cryptography, progress slowed until Hellman and Diffie introduced their paper involving "state-supported-key cryptography".[32]
An encryption standard [edit]
The mid-1970s saw two major public (i.e., non-secret) advances. First was the publication of the conscription Data Encryption Standard in the U.S. Federal Read on 17 Border district 1975. The proposed DES cipher was submitted by a research chemical group at IBM, at the invitation of the Position Bureau of Standards (now NIST), in an effort to uprise secure lepton communication facilities for businesses such A banks and other spacious financial organizations. After advice and qualifying aside the NSA, acting behind the scenes, IT was adopted and published as a Federal Information Processing Standard Publication in 1977 (presently at FIPS 46-3). DES was the first of all in public accessible cipher to live 'blessed' aside a national agency such as the National Security Agency. The release of its specification by NBS stimulated an explosion of national and academic concern in cryptography.
The aging Diethylstilboestrol was officially replaced away the Advanced Encryption Standard (AES) in 2001 when NIST proclaimed FIPS 197. Afterwards an open competition, NIST selected Rijndael, submitted by 2 Belgian cryptographers, to atomic number 4 the AES. Diethylstilbestrol, and many secure variants of it (such as Triple DES), are nonetheless used today, having been merged into many national and organizational standards. However, its 56-bit key-size has been shown to be insufficient to ward against brute force attacks (one such attack, undertaken by the cyber civil-rights grouping Electronic Frontier Instauratio in 1997, succeeded in 56 hours.[33]) As a leave, use of straight DES encryption is right away no doubt insecure for use in new cryptosystem designs, and messages preserved away older cryptosystems using DES, and indeed all messages sent since 1976 using DES, are also at risk. Regardless of DES' inherent quality, the DES key sizing (56-bits) was idea to be too small by more or less even in 1976, perhaps most publically by Whitfield Diffie. In that respect was suspicion that regime organizations even then had decent computing power to break DES messages; intelligibly others have achieved this capability.
Public identify [edit]
The second developing, in 1976, was perhaps even many important, for it fundamentally changed the way cryptosystems might process. This was the issue of the paper New Directions in Coding by Whitfield Diffie and Martin Hellman. It introduced a radically new method of distributing cryptographic keys, which went far toward solving unrivaled of the fundamental problems of cryptography, key statistical distribution, and has become known As Diffie–Hellman key exchange. The article besides stimulated the virtually direct public development of a new class of enciphering algorithms, the asymmetric operative algorithms.
Prior to that time, wholly multipurpose moderne encryption algorithms had been symmetric central algorithms, in which the same science key out is in use with the underlying algorithm by both the sender and the recipient, who must some keep IT undercover. All of the electromechanical machines used in World War II were of this sensible class, American Samoa were the Gaius Julius Caesar and Atbash ciphers and essentially all cipher systems end-to-end history. The 'key' for a encode is, of course, the codebook, which must as wel be distributed and kept secret, and so shares most of the same problems in exercise.
Of necessity, the key in every such scheme had to embody exchanged between the communicating parties in some secure elbow room prior to any use of the system (the full term unremarkably used is 'via a secure channel') such A a trustworthy courier with a briefcase handcuffed to a wrist joint, operating room face-to-face contact, operating room a loyal carrier pigeon. This requirement is ne'er trivial and very rapidly becomes unmanageable Eastern Samoa the number of participants increases, or when safety-deposit channels aren't available for primal telephone exchange, operating theatre when, as is sensitive cryptographic practice, keys are ofttimes changed. Particularly, if messages are meant to be moated from other users, a separate of import is required for to each one workable pair of users. A organisation of this kind is known American Samoa a secret key, or trigonal key cryptosystem. D-H winder exchange (and succeeding improvements and variants) made operation of these systems often easier, and more secure, than had ever been possible in front in all of history.
In contrast, asymmetric Francis Scott Key encryption uses a pair of mathematically related keys, for each one of which decrypts the encoding performed using the other. Some, but not all, of these algorithms have the extra property that one of the matched keys cannot represent deduced from the new by any known method differently trial and computer error. An algorithmic program of this kind is called a public significant or irregular headstone system. Using so much an algorithm, only one key pair is needed per user. By designating one key of the pair As private (always secret), and the other as public (often widely available), no secure transmission channel is required for key exchange. So long as the private key corset classified, the unrestricted key can be widely known for a same long time without compromising security measures, devising it safe to reuse the same key pair indefinitely.
For two users of an asymmetric key algorithm to communicate securely over an insecure canalise, each user will need to know their own public and private keys also as the other user's public key. Take this basic scenario: Alice and Bob each have a twin of keys they've been using for long time with many strange users. At the start of their subject matter, they switch public keys, unencrypted over an insecure line. Alice then encrypts a message using her private key, and then re-encrypts that result using Bob's unexclusive key. The double-encrypted message is then sent as integer data over a wire from Alice to Bobsleigh. Bob receives the bit stream and decrypts IT using his own private key, and so decrypts that bit stream using Alice's public key. If the final result is recognizable as a message, Bob can be confident that the message actually came from someone who knows Alice's private key (presumptively in reality her if she's been careful with her private key), and that anyone eavesdropping on the channel testament need Bob's private key in order to infer the substance.
Unsymmetric algorithms rely for their effectiveness on a class of problems in mathematics called one-way functions, which require comparatively little computational mightiness to execute, just large amounts of power to reverse, if reversal is possible at all. A classic example of a one-way officiate is propagation of very large prime numbers. It's reasonably quick to reproduce two large primes, but very difficult to find the factors of the product of two oversize primes. Because of the mathematics of one-way functions, most possible keys are bad choices as cryptographic keys; exclusive a small fraction of the possible keys of a given length are suitable, and so asymmetric algorithms require identical long keys to reach the same level of security provided by relatively shorter symmetric keys. The need to some engender the key pairs, and perform the encoding/decoding operations make unsymmetrical algorithms computationally expensive, compared to most symmetric algorithms. Since symmetric algorithms can often use any sequence of (random, surgery at least aleatory) bits as a key, a available session key can be quickly generated for unawares-term function. Consequently, it is common practice to usage a long lopsided key to exchange a disposable, untold shorter (but just as efficacious) symmetric key. The slower asymmetric algorithm securely sends a symmetric session key, and the faster symmetric algorithm takes terminated for the remainder of the message.
Asymmetric key cryptography, Diffie–Hellman key exchange, and the best known of the public key out / private key algorithms (i.e., what is usually named the RSA algorithm), all seem to have been independently matured at a UK intelligence before the public announcement by Diffie and Hellman in 1976. GCHQ has released documents claiming they had formed public of import cryptography ahead the publication of Diffie and Hellman's newspaper.[ commendation requisite ] Diverse classified papers were written at GCHQ during the 1960s and 1970s which eventually led to schemes essentially indistinguishable to RSA encryption and to Diffie–Hellman key exchange in 1973 and 1974. Some of these have now been published, and the inventors (James H. Ellis, Clifford Cocks, and Malcolm Williamson) have made public (some of) their exercise.
Hashing [edit]
Hashing is a public technique old in cryptography to encode information quickly using typical algorithms. Generally, an algorithm is practical to a string of text, and the resulting string becomes the "hash value". This creates a "digital fingerprint" of the message, as the specific hash value is accustomed identify a taxonomic category content. The output from the algorithm is also referred to As a "message digest" or a "check total". Hashing is peachy for determining if information has been changed in transmission. If the hash esteem is different upon reception than upon sending, there is evidence the message has been altered. Once the algorithm has been applied to the data to be hashed, the haschisc function produces a fixed-duration production. Basically, anything passed through the hash function should resolve to the assonant length output American Samoa anything else passed through the cookie-cutter hasheesh function. Information technology is important to note that hashing is non the same as encrypting. Hashing is a unidirectional operation that is used to transform data into the compressed message support. Additionally, the integrity of the message can be measured with hashing. Conversely, encryption is a bipartite surgical process that is misused to transform plaintext into cipher-textual matter so vice versa. In encryption, the confidentiality of a message is guaranteed.[34]
Hash functions can be wont to verify integer signatures, so that when signing documents via the Internet, the signature is applied to cardinal particular individual. Much like a hand-written signature, these signatures are verified by assigning their exact hash encipher to a person. Furthermore, hashing is practical to passwords for computing device systems. Hashing for passwords began with the UNIX OS. A drug user connected the system would first create a password. That password would be hashed, victimisation an algorithm Beaver State key, then stored in a word file. This is still prominent now, as web applications that require passwords will often hashish drug user's passwords and store them in a database.[35]
Cryptography politics [edit]
The national developments of the 1970s poor the draw close Monopoly on high quality cryptography held by government organizations (see S Levy's Crypto for a print media account of some of the policy controversy of the time in the US). For the first time ever so, those outside government organizations had access to secret writing not readily breakable by anyone (including governments). Considerable controversy, and dispute, both national and private, began more Beaver State little immediately, sometimes called the crypto wars. They have not withal subsided. In many countries, e.g., export of cryptography is subject to restrictions. Until 1996 exportation from the U.S. of cryptography victimization keys longer than 40 bits (too small to live very promised against a knowledgeable assaulter) was precipitously limited. As recently as 2004, former FBI Director Joe Louis Freeh, testifying before the 9/11 Commission, titled for new laws against public use of encryption.
One of the most important people favoring strong encoding for national use was Phil Zimmermann. He wrote and then in 1991 released PGP (Jolly Salutary Privacy), a very high superior crypto organisation. He distributed a freeware rendering of PGP when he felt threatened by legislation and so below consideration by the US Government that would require backdoors to be included in all cryptographic products developed within the US. His arrangement was released worldwide briefly after he free it in the USA, and that began a tenacious criminal investigating of him by the US Political science Justice Department for the declared violation of export restrictions. The Justice Department in time dropped its case against Zimmermann, and the freeware distribution of PGP has continued around the world. PGP even sooner or later became an open Internet standard (RFC 2440 or OpenPGP).
Moderne cryptography [delete]
Spell mod ciphers like AES and the higher prize asymmetric ciphers are wide well-advised unbreakable, poor designs and implementations are still sometimes adopted and thither rich person been important cryptanalytic breaks of deployed crypto systems in recent years. Famed examples of broken crypto designs admit the first WI-Fi encryption scheme WEP, the Content Scrambling System victimised for encrypting and controlling Videodisk use, the A5/1 and A5/2 ciphers used in GSM cellular phone phones, and the CRYPTO1 cryptograph used in the widely deployed MIFARE Standard smart cards from NXP Semiconductors, a spun turned class of Philips Electronics. All of these are symmetric ciphers. Hitherto, not united of the mathematical ideas underlying public key cryptography has been evidenced to follow 'unbreakable', and then some future tense mathematical analysis kick upstairs might give systems relying on them insecure. While few informed observers foresee so much a breakthrough, the key size of it recommended for security system as best practice keeps exploding as accumulated computing power required for breaking codes becomes cheaper and much uncommitted. Quantum computers, if ever constructed with sufficiency capacity, could break existing public samara algorithms and efforts are underway to prepare and standardize spot-quantum cryptography.
Even without breaking encoding in the traditional horse sense, side-transmit attacks stool be mounted that exploit information gained from the way a computer system is implemented, such as cache retentivity usage, timing information, power consumption, magnetism leaks or even sounds emitted. Newer cryptological algorithms are being formed that make such attacks more difficult.
See also [edit]
- National Security Agency encryption systems
- Coding
- Timeline of cryptography
- Topics in cryptanalysis
- Japanese cryptology from the 1500s to Meiji
- Creation War I steganography
- World War II cryptography
- List of cryptographers
- Category:Undeciphered liberal arts codes and ciphers
References [edit]
- ^ a b c d "A Brief History of Cryptography". Cypher Research Laboratories. 24 January 2006. Retrieved 18 September 2013.
- ^ "Cryptography in Ancient Civilizations". Retrieved 18 Sept 2013. [ permanent drained link ]
- ^ Kahn, David. The Codebreakers: A Comprehensive History of Secret Communication from Antediluvian Times to the Internet, Revised and Updated. Scribner. New York, Inexperient York. 1996.
- ^ "A Short History of Cryptography." Cryptozine. 16 May 2008.
- ^ a b c "2.1 - A Sawed-off History of Cryptography". all.net . Retrieved 19 Border 2018.
- ^ Translators: Richard Burton, Bhagavanlal Indrajit, Shivaram Parashuram Bhide (18 January 2009). The Kama Sutra of Vatsyayana (Translated From The Sanscrit in Seven Parts With Foreword,Founding and Concluding Remarks). The Project Gutenberg. Retrieved 3 December 2015. CS1 maint: multiple names: authors list (link)
- ^ David Kahn (December 1996). The Codebreakers. Simon and Schuster. p. 74. ISBN9781439103555 . Retrieved 25 November 2015.
- ^ Hans Dieter Betz (1992). "The Greek Magical Papyri in Translation, Including the Demotic Spells, Volume 1".
- ^ "Story of Encryption". SANS.
- ^ Kelly, Thomas. "The Myth of the Skytale." Cryptologia 22.3 (1998): 244–260.
- ^ Lateiner, D. "Signifying Names and Other Inauspicious Accidental Utterances in Classical Historiography." Grecian, Romanic, and Geographic area Studies 45.1 (2010): 35–57. Print.
- ^ icitsuser (22 January 2017). "The Ancient Cryptography History". ICITS . Retrieved 7 Apr 2019.
- ^ Kahn, Jacques Louis David (1996). The Codebreakers: The Comprehensive History of Secret Communication from Ancient Times to the Internet. Simon and Schuster. ISBN9781439103555.
- ^ a b Broemeling, Lyle D. (1 November 2011). "An Calculate of Early Statistical Inference in Arab Cryptology". The American Statistician. 65 (4): 255–257. doi:10.1198/tas.2011.10191. S2CID 123537702.
- ^ Leaman, Joseph Oliver (16 July 2015). The Story Encyclopedia of Islamic Philosophy. Bloomsbury Publication. ISBN9781472569455.
- ^ Al-Jubouri, I. M. N. (19 March 2018). Chronicle of Monotheism Philosophy: With View of Greek School of thought and Premature History of Mohammedanism. Authors happening Line Ltd. ISBN9780755210114.
- ^ Simon Singh, The Computer code Book, pp. 14–20
- ^ "Al-Kindi, Cryptgraphy, Codebreaking and Ciphers". Retrieved 12 Jan 2007.
- ^ Ibrahim A. Al-Kadi (April 1992), "The origins of cryptology: The Arab contributions", Cryptologia 16 (2): 97–126
- ^ Saltzman, Gum benjamin A. "Ut hkskdkxt: Early Medieval Cryptography, Textual Errors, and Scribal Agency (Speculum, extroverted)". Speculum.
- ^ David Salamon Coding for Data and Computer Communications. Springer, 2006.
- ^ Henry Martyn Robert Hooke (1705). The Posthumous Works of Hooke. Richard Waller, London. p. 203.
- ^ Lund, Paul (2009). The Book of Codes. Berkeley and Los Angeles, California: University of Golden State Constrict. pp. 106–107. ISBN9780520260139.
- ^ Silverman, Kenneth. Edgar A. Poe: Mournful and Never-ending Remembrance. NY: Harper Perennial, 1991. p. 152-3
- ^ "Infographic - The History of Encoding". www.come forth.com . Retrieved 19 March 2018.
- ^ Fenton, Ben (22 June 2006). "Enigma and the British code of honour". The Daily Telegraphy. London. Archived from the original on 15 December 2007.
- ^ Fessenden, Marissa (27 January 2015). "Women Were Key to WWII Code-Break at Bletchley Park". Smithsonian Magazine. Retrieved 10 May 2019.
At its height there were to a higher degree 10,000 populate working at Bletchley Park, of whom more than two-thirds were women.
- ^ a b Mundy, Liza (2017). Code Girls: The Untold Report of the American Women Encode Surf of World War II. Hot York, Boston: Hachette Books. ISBN978-0-316-35253-6.
- ^ Froomkin, Dan (8 May 1998). "Deciphering Encryption". The Washington Post . Retrieved 18 September 2013.
- ^ Shelton Jackson Lee, Tom (August 2000). "Cryptography and the New Economy" (PDF). The Industrial Physicist. 6 (4): 31. Archived from the daring (PDF) on 16 Feb 2012. Retrieved 18 September 2013.
- ^ Communication theory of secrecy systems, Claude Claude Shannon, 1949
- ^ a b c Berlekamp, Elwyn; Solomon W. Golomb; Thomas M. Cover; Robert G. Gallager; James L. Massey; Andrew J. Viterbi (January 2002). "Claude Elwood Shannon (1916–2001)" (PDF). Notices of the AMS. 49 (1): 8–16. Retrieved 18 September 2013.
- ^ Natural philosophy Frontier Foundation, Cracking DES, O'Reilly, 1998.
- ^ Shon Harris. "Cryptography" (PDF). Archived from the original (PDF) on 15 September 2012. Retrieved 18 September 2013.
- ^ Grah, Joseph Sterling. "Hash Functions in Coding" (PDF) . Retrieved 18 September 2013.
Outer links [edit]
- Helger Lipmaa's cryptography pointers
- Timeline of cipher machines
Where Dis the Dicision 2 Cipher Key Come From
Source: https://en.wikipedia.org/wiki/History_of_cryptography
Belum ada Komentar untuk "Where Dis the Dicision 2 Cipher Key Come From"
Posting Komentar